Step-by-Step Guide: Setting Up WordPress with Nginx on Ubuntu 24.04 (LTS)
1. Create and Secure a Virtual Private Server
2. Install Nginx PHP 8.3 WP-CLI MySQL
3. Setting Up WordPress with SSL on Nginx
(Current Step) 4. Set Up Free SSL/TLS with Cloudflare to Nginx (Skip this if you using Certbot in Step 3)
5. Set Up Redis Object Cache and Nginx FastCGI Page Cache
Prerequisite
- A VM (virtual machine) on any hosting service such as Cloud provider (GCP, AWS, Azure) or VPS provider (DigitalOcean, Vultr) running Nginx, PHP and MySQL.
- Creating a Cloudflare account is free.
- A Domain name and to point its DNS records to your NGINX server on Cloudflare, check them out here.
Alright, once you have everything we mentioned ready, let’s jump into the tutorial.
Cloudflare
Cloudflare offers powerful features, for free! Let’s explore setting up SSL in this article.
Even if your domain isn’t registered with Cloudflare, you can still leverage their free DNS service and SSL certificate. This gives you more control over your domain’s settings and adds a layer of security to your website.
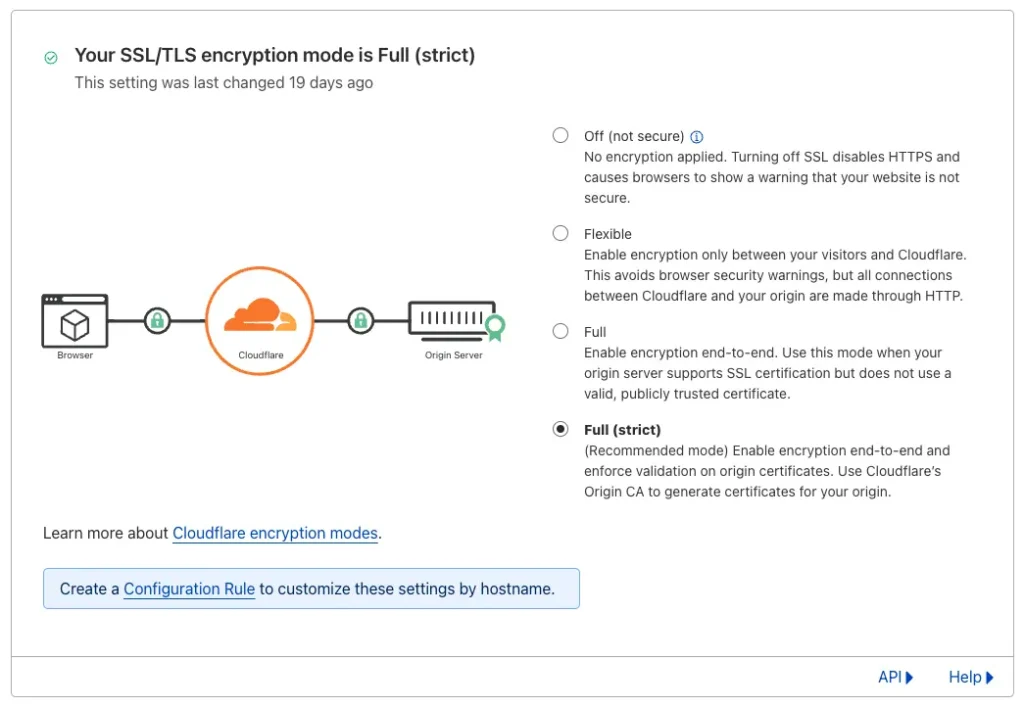
- Flexible: This mode offers partial security. While the connection between your visitors and Cloudflare is encrypted (HTTPS), the connection between Cloudflare and your server remains unencrypted (HTTP). This means information exchanged between them might be visible to potential attackers.
- Full: Provides complete security. All communication between your visitors, Cloudflare, and your server is encrypted (HTTPS).
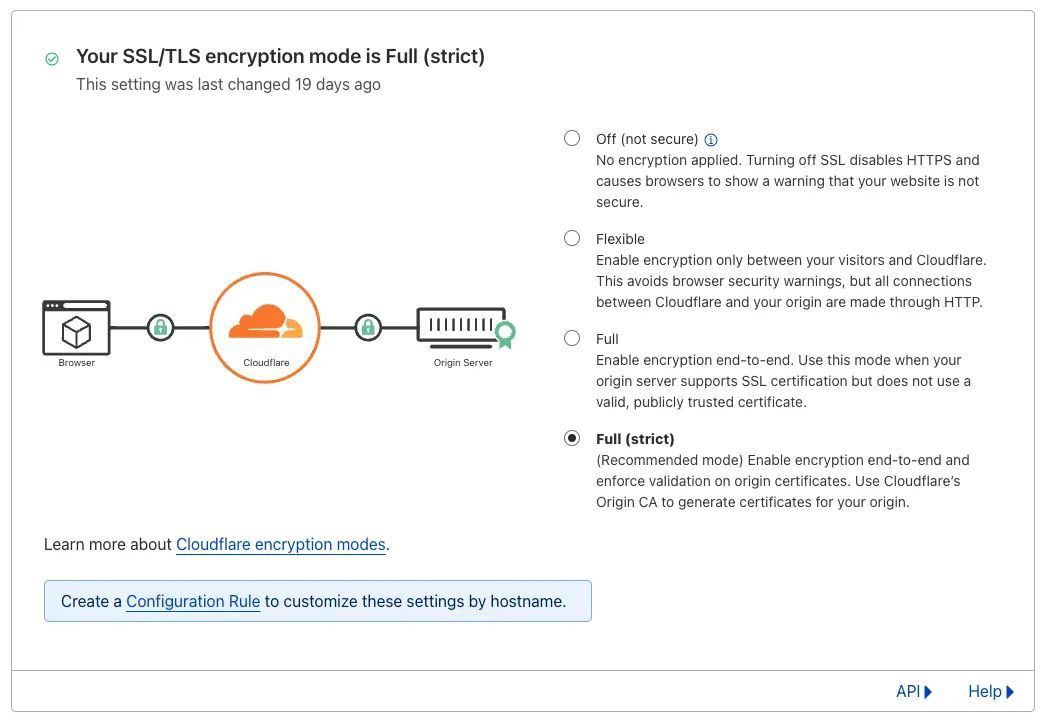
- Full (strict): This builds upon Full SSL by adding an extra layer of security for the connection between Cloudflare and your server. It ensures this connection is encrypted using a certificate issued by a trusted Certificate Authority (CA) or Cloudflare’s own Origin CA. This provides the highest level of security for your website. We’ll cover how to set up Full (strict) SSL later in this article.
1. Create Origin Certificate
Cloudflare offers a free SSL certificate you can install on your Nginx server. This establishes an encrypted connection for data transfer between Cloudflare and your server.
- In the SSL/TLS section, navigate to “Origin Server” and create a new certificate.
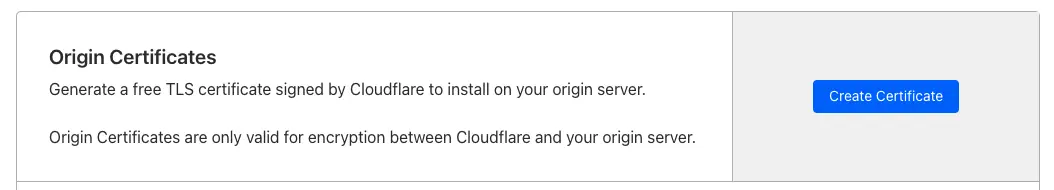
- Click Create to generate your certificate.
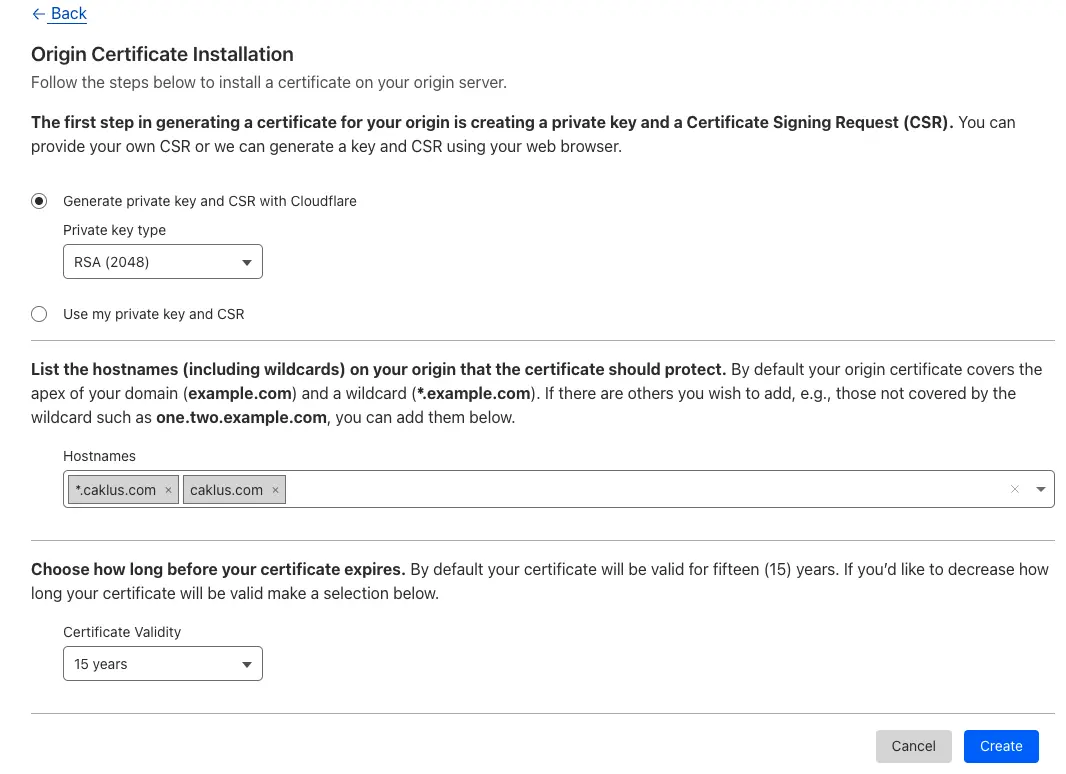
- Once you generate the certificate, keep a copy of the private key in a safe and secure location. You won’t be able to access it again after clicking “OK” to download the certificate. Then, proceed with installing the certificate on your Nginx server.
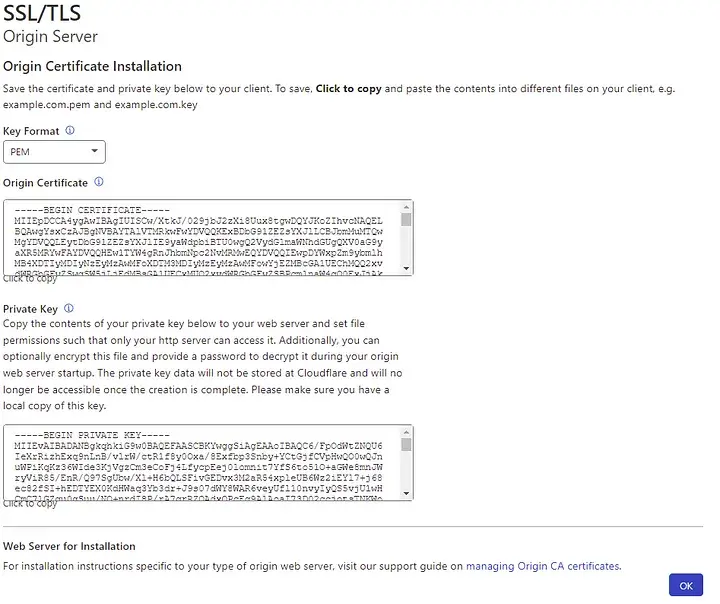
- First create directory for save Origin Certificate and Private Key.
sudo mkdir /etc/ssl/cloudflare
sudo mkdir /etc/ssl/cloudflare/caklus.com- Copy Origin Certificate to /etc/ssl/cloudflare/caklus.com/cert.pem on your server and save (Ctrl+X, Y then hit Enter).
sudo nano /etc/ssl/cloudflare/caklus.com/cert.pem- Then Copy Private Key to /etc/ssl/cloudflare/caklus.com/key.pem on your server and save (Ctrl+X, Y then hit Enter).
sudo nano /etc/ssl/cloudflare/caklus.com/key.pem- Configure your server to verify Cloudflare’s identity for secure origin communication.
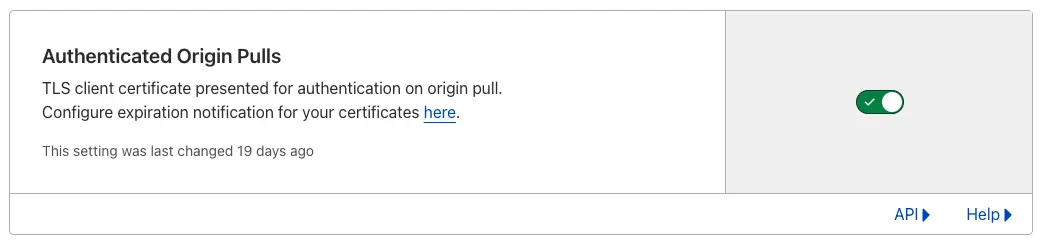
Authenticated Origin Pulls allow you to cryptographically verify that requests to your origin server have come from Cloudflare using a TLS client certificate. This prevents clients from sending requests directly to your origin, bypassing security measures provided by Cloudflare, such as IP and Web Application Firewalls, logging, and encryption.
Refer More: https://developers.cloudflare.com/ssl/origin-configuration/authenticated-origin-pull - Add the Cloudflare TLS client certificate to our Nginx server:
sudo nano /etc/ssl/certs/cloudflare.crt- Copy this Certificate to /etc/ssl/certs/cloudflare.crt on your server and save (Ctrl+X, Y then hit Enter).
-----BEGIN CERTIFICATE-----
MIIGCjCCA/KgAwIBAgIIV5G6lVbCLmEwDQYJKoZIhvcNAQENBQAwgZAxCzAJBgNV
BAYTAlVTMRkwFwYDVQQKExBDbG91ZEZsYXJlLCBJbmMuMRQwEgYDVQQLEwtPcmln
aW4gUHVsbDEWMBQGA1UEBxMNU2FuIEZyYW5jaXNjbzETMBEGA1UECBMKQ2FsaWZv
cm5pYTEjMCEGA1UEAxMab3JpZ2luLXB1bGwuY2xvdWRmbGFyZS5uZXQwHhcNMTkx
MDEwMTg0NTAwWhcNMjkxMTAxMTcwMDAwWjCBkDELMAkGA1UEBhMCVVMxGTAXBgNV
BAoTEENsb3VkRmxhcmUsIEluYy4xFDASBgNVBAsTC09yaWdpbiBQdWxsMRYwFAYD
VQQHEw1TYW4gRnJhbmNpc2NvMRMwEQYDVQQIEwpDYWxpZm9ybmlhMSMwIQYDVQQD
ExpvcmlnaW4tcHVsbC5jbG91ZGZsYXJlLm5ldDCCAiIwDQYJKoZIhvcNAQEBBQAD
ggIPADCCAgoCggIBAN2y2zojYfl0bKfhp0AJBFeV+jQqbCw3sHmvEPwLmqDLqynI
42tZXR5y914ZB9ZrwbL/K5O46exd/LujJnV2b3dzcx5rtiQzso0xzljqbnbQT20e
ihx/WrF4OkZKydZzsdaJsWAPuplDH5P7J82q3re88jQdgE5hqjqFZ3clCG7lxoBw
hLaazm3NJJlUfzdk97ouRvnFGAuXd5cQVx8jYOOeU60sWqmMe4QHdOvpqB91bJoY
QSKVFjUgHeTpN8tNpKJfb9LIn3pun3bC9NKNHtRKMNX3Kl/sAPq7q/AlndvA2Kw3
Dkum2mHQUGdzVHqcOgea9BGjLK2h7SuX93zTWL02u799dr6Xkrad/WShHchfjjRn
aL35niJUDr02YJtPgxWObsrfOU63B8juLUphW/4BOjjJyAG5l9j1//aUGEi/sEe5
lqVv0P78QrxoxR+MMXiJwQab5FB8TG/ac6mRHgF9CmkX90uaRh+OC07XjTdfSKGR
PpM9hB2ZhLol/nf8qmoLdoD5HvODZuKu2+muKeVHXgw2/A6wM7OwrinxZiyBk5Hh
CvaADH7PZpU6z/zv5NU5HSvXiKtCzFuDu4/Zfi34RfHXeCUfHAb4KfNRXJwMsxUa
+4ZpSAX2G6RnGU5meuXpU5/V+DQJp/e69XyyY6RXDoMywaEFlIlXBqjRRA2pAgMB
AAGjZjBkMA4GA1UdDwEB/wQEAwIBBjASBgNVHRMBAf8ECDAGAQH/AgECMB0GA1Ud
DgQWBBRDWUsraYuA4REzalfNVzjann3F6zAfBgNVHSMEGDAWgBRDWUsraYuA4REz
alfNVzjann3F6zANBgkqhkiG9w0BAQ0FAAOCAgEAkQ+T9nqcSlAuW/90DeYmQOW1
QhqOor5psBEGvxbNGV2hdLJY8h6QUq48BCevcMChg/L1CkznBNI40i3/6heDn3IS
zVEwXKf34pPFCACWVMZxbQjkNRTiH8iRur9EsaNQ5oXCPJkhwg2+IFyoPAAYURoX
VcI9SCDUa45clmYHJ/XYwV1icGVI8/9b2JUqklnOTa5tugwIUi5sTfipNcJXHhgz
6BKYDl0/UP0lLKbsUETXeTGDiDpxZYIgbcFrRDDkHC6BSvdWVEiH5b9mH2BON60z
0O0j8EEKTwi9jnafVtZQXP/D8yoVowdFDjXcKkOPF/1gIh9qrFR6GdoPVgB3SkLc
5ulBqZaCHm563jsvWb/kXJnlFxW+1bsO9BDD6DweBcGdNurgmH625wBXksSdD7y/
fakk8DagjbjKShYlPEFOAqEcliwjF45eabL0t27MJV61O/jHzHL3dknXeE4BDa2j
bA+JbyJeUMtU7KMsxvx82RmhqBEJJDBCJ3scVptvhDMRrtqDBW5JShxoAOcpFQGm
iYWicn46nPDjgTU0bX1ZPpTpryXbvciVL5RkVBuyX2ntcOLDPlZWgxZCBp96x07F
AnOzKgZk4RzZPNAxCXERVxajn/FLcOhglVAKo5H0ac+AitlQ0ip55D2/mf8o72tM
fVQ6VpyjEXdiIXWUq/o=
-----END CERTIFICATE-----You can also download the Certificate from here.
2. Configure Nginx to host your website
Now that you’ve created and copied the certificate and private key to your server, it’s time to configure Nginx to use them.
- Ensure you’re currently in your home directory
cd ~/- To organize your WordPress site, create folders named logs for Nginx logs and public to hold all website files.
mkdir -p caklus.com/logs caklus.com/public
chmod -R 755 caklus.com- For a clean setup, we’ll manage your websites within your home directory using a structured folder hierarchy.
newuser@tutorial:~$ ls -l ~/caklus.com
total 8
drwxr-xr-x 2 newuser newuser 4096 Jul 10 15:38 logs
drwxr-xr-x 2 newuser newuser 4096 Jul 10 15:38 public- Since we’ve created the necessary folders, let’s head to the sites-available directory and configure the Nginx server block.
cd /etc/nginx/sites-available- To keep things organized, use the same name for your website’s root directory and its configuration file.
sudo nano caklus.com- Paste the configuration, replace highlighted text with your website details (domain, log paths, root directory, Origin Certificate, Private Key, ssl_verify_client and ssl_client_certificate), and save (Ctrl+X, Y then hit Enter).
server {
listen 443 ssl;
listen [::]:443 ssl;
http2 on;
server_name caklus.com;
ssl_certificate /etc/ssl/cloudflare/caklus.com/cert.pem;
ssl_certificate_key /etc/ssl/cloudflare/caklus.com/key.pem;
ssl_verify_client on;
ssl_client_certificate /etc/ssl/certs/cloudflare.crt;
access_log /home/newuser/caklus.com/logs/access.log;
error_log /home/newuser/caklus.com/logs/error.log;
root /home/newuser/caklus.com/public/;
index index.php;
location / {
try_files $uri $uri/ /index.php?$args;
}
location ~ \.php$ {
try_files $uri =404;
fastcgi_split_path_info ^(.+\.php)(/.+)$;
fastcgi_pass unix:/run/php/php8.3-fpm.sock;
fastcgi_index index.php;
include fastcgi.conf;
}
}
server {
listen 443 ssl;
listen [::]:443 ssl;
http2 on;
server_name www.caklus.com;
ssl_certificate /etc/ssl/cloudflare/caklus.com/cert.pem;
ssl_certificate_key /etc/ssl/cloudflare/caklus.com/key.pem;
ssl_verify_client on;
ssl_client_certificate /etc/ssl/certs/cloudflare.crt;
return 301 https://caklus.com$request_uri;
}
server {
listen 80;
listen [::]:80;
server_name caklus.com www.caklus.com;
return 301 https://caklus.com$request_uri;
}- Activate your new site with a simple shortcut: ln -s /path/to/your/file /etc/nginx/sites-enabled/your_file.conf
sudo ln -s /etc/nginx/sites-available/caklus.com /etc/nginx/sites-enabled/caklus.com- Before restarting Nginx to activate the changes, let’s double-check everything for errors.
sudo nginx -t- Fix any errors found during the test (if any), then restart Nginx to activate your site.
sudo service nginx reload- In the SSL/TLS section, enable Full (strict) mode under Overview.
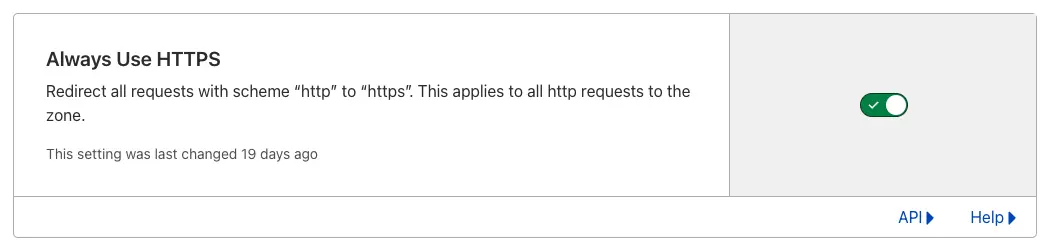
- In the SSL/TLS section, enable Always Use HTTPS under Edge Certificate to automatically redirect HTTP traffic to HTTPS.
- To complete the setup, enable Authenticated Origin Pulls. Then, navigate to the SSL/TLS section, choose Origin Server, and turn it on.
To verify the configuration, open your web browser and navigate to https://example.com. Look for a secure connection indicator (usually a padlock icon) to confirm successful setup.





